System Security and User Access
Prodigy makes it easy for the user to find the facilities they need. Its configurable menu system provides direct and secure access not only to Prodigy facilities but also to other Windows applications.
Prodigy can also provide the highest levels of user security, data security and audit trail for FDA 21 CFR Part 11 and similar regulations
Menu Selection
Access to Prodigy is provided via a Menu Bar which can be docked against any edge of the screen and can be made to auto-hide, like the Windows taskbar.
The menu layout can be configured using the built in graphical editor and these menus can be used to launch not only Prodigy components, but also any desktop application that runs under Windows.
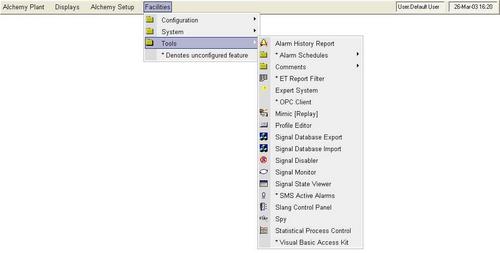
When creating the menu layout, whole menus or individual items may be protected against unauthorised access.
System Security
|
|
Access & SecurityAccess to Prodigy and standard desktop applications via a configurable menu bar. Security may be applied to any item that requires input from the operator, thus preventing unauthorised access of such things as accepting alarms through changing setpoints to reconfiguring the database. |
Prodigy provides two types of security:
- A simple password, which everyone who wishes to access this item must know.
- A privilege based system whereby individual users may be assigned a range of privileges to allow them access to particular aspects of the system.
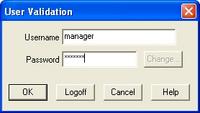
Operators may log on to the Prodigy system to gain instant access to the features for which they hold privileges. Alternatively, they may enter their user ID and password each time they access a feature for which the current user is not privileged.
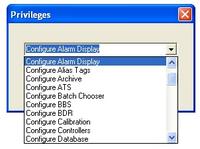
Prodigy supports the idea of a "Default User" which may be enabled with a limited set of privileges, perhaps providing "view only" access to the system. In the absence of any other user being logged in, it is the privileges assigned to the default user that are applied.
Prodigy comes with a set of standard privileges that can be used to restrict access to certain facilities. It also allows you to create your own privilege types to provide further access limitations as required.
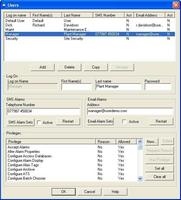
The user database can also hold a mobile phone number and email address for each user, which will be used to send alarms and reports to user phones or PC's using Prodigy's SMS text message and email facilities.
Windows Destop Lockdown
A Lockdown Tab is provided that allows quick and easy configuration of the computer desktop (not Prodigy) so that access is allowed only to those aspects of the desktop that you want to allow. This will prevent the users of the Prodigy system from gaining access to Explorer, system tools, games, the internet, network resources and so on. This kind of lockdown is recommended in many application areas where you want to prevent “tampering” with the system, either intentional or otherwise.
Enhanced Security
Users that need highly secure SCADA systems, including food, drink, pharmaceutical and related industries affected by FDA 21 CFR Part 11 regulations, can benefit from Prodigy's "one tick" approach towards compliance.
These facilities are designed to aid validation and compliance within the requirements of FDA 21 CFR Part 11, GAMP and GLP. These facilities can be easily configured to provide high security SCADA systems for any industry.
